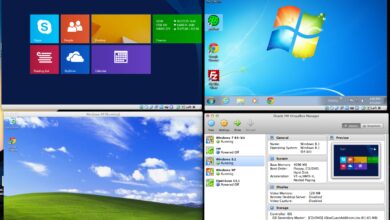
System Files: 7 Ultimate Secrets Revealed for Power Users
Ever wondered what keeps your computer running smoothly behind the scenes? It’s not magic—it’s system files doing the heavy lifting. These hidden digital gears are essential for your OS to function, and understanding them can unlock powerful control over your machine.
What Are System Files and Why They Matter

System files are the backbone of any operating system. They’re not just random bits of code; they’re carefully designed components that enable your computer to boot, run applications, manage hardware, and maintain stability. Without them, your device would be nothing more than expensive hardware with no soul.
The Core Definition of System Files
System files are pre-installed files created by the operating system (OS) developer—like Microsoft, Apple, or Linux distributors—that are essential for the OS to operate. These include executable files, configuration files, drivers, libraries, and bootloaders. They are typically stored in protected directories such as C:WindowsSystem32 on Windows or /usr/bin and /etc on Linux.
- They are automatically loaded during startup.
- They manage communication between hardware and software.
- They enforce security policies and user permissions.
Different Types of System Files
Not all system files serve the same purpose. They come in various formats and functions:
.dll (Dynamic Link Libraries): Shared libraries used by multiple programs in Windows..sys: Device driver files in Windows that interface with hardware..ini, .cfg, .conf: Configuration files that store settings for the OS or applications.vmlinuz, initrd.img: Linux kernel and initial RAM disk images critical for booting.bootmgr, BCD: Boot configuration data files in Windows that manage the startup process.
.”System files are like the DNA of your operating system—they contain the instructions that define how your computer behaves.” — TechTarget, https://www.techtarget.com
How System Files Differ from Regular Files
Unlike user-created documents or media files, system files are protected by the OS.They often have hidden attributes and restricted permissions to prevent accidental deletion or modification.For example, in Windows, you need administrator rights to modify files in the System32 folder.In Unix-like systems, root access is required..
- System files are marked as hidden and system (H+S attributes in Windows).
- They are usually signed digitally to ensure authenticity.
- Modifying them without proper knowledge can lead to system instability or failure.
How System Files Work Behind the Scenes
When you press the power button, a complex chain of events begins—all orchestrated by system files. From the BIOS handshake to loading the kernel, every step relies on specific files working in harmony. Understanding this process demystifies how your computer comes to life.
The Boot Process and System Files
The boot sequence is one of the most critical phases where system files take center stage. Here’s a simplified breakdown:
- BIOS/UEFI: Initializes hardware and looks for a bootable device.
- Bootloader (e.g., NTLDR, GRUB): Loads the OS kernel into memory. GRUB, for instance, reads
/boot/grub/grub.cfgon Linux systems. - Kernel (ntoskrnl.exe, vmlinuz): The core of the OS, responsible for memory management, process scheduling, and hardware abstraction.
- System Services: Initiated by
smss.exein Windows orsystemdin Linux, these services start essential background processes.
Each of these stages depends on specific system files. A corrupted bootmgr can render your PC unbootable.
Role of System Files in OS Operations
Once the system is up and running, system files continue to manage daily operations:
- Registry (Windows): The
SYSTEMandSOFTWAREhives inC:WindowsSystem32configstore configuration data. - Device Drivers (.sys, .ko): Enable communication with peripherals like printers, GPUs, and network cards.
- System Libraries (DLLs, .so files): Provide reusable code for applications, reducing redundancy.
- Scheduled Tasks and Services: Managed by files like
taskschd.mscandservices.exe.
For example, when you open a web browser, multiple system files are invoked to allocate memory, render graphics, and manage network connections.
File Protection Mechanisms in Modern OS
To prevent tampering, modern operating systems employ robust protection mechanisms:
- Windows File Protection (WFP): Prevents unauthorized changes to critical system files. If a protected file is altered, WFP restores it from a cached copy.
- TrustedInstaller (Windows): The highest-level service account that owns core system files, limiting even admin access.
- System Integrity Protection (SIP) in macOS: Protects system directories like
/Systemand/binfrom modification, even by root. - Immutable File Attributes (Linux): Using
chattr +ito make files undeletable.
These safeguards are crucial for security, especially against malware that targets system files to gain persistence.
Common System Files in Windows, macOS, and Linux
Each operating system has its own set of critical system files. Knowing which ones are essential can help you troubleshoot issues or understand system behavior.
Essential System Files in Windows
Windows relies on a vast array of system files. Some of the most important include:
- ntoskrnl.exe: The Windows kernel, responsible for core OS functions.
- hal.dll: Hardware Abstraction Layer, bridges the kernel and hardware.
- winlogon.exe: Manages user logins and the secure attention sequence (Ctrl+Alt+Del).
- lsass.exe: Handles login authentication and security policies.
- smss.exe: Session Manager Subsystem, one of the first processes started during boot.
- explorer.exe: The shell that provides the desktop interface.
These files reside in C:WindowsSystem32 and are protected by Windows Resource Protection (WRP).
Key System Files in macOS
macOS, being Unix-based, shares similarities with Linux but has unique components:
- mach_kernel: The core of the XNU kernel used in older macOS versions.
- launchd: The first process (PID 1) that starts all system services and daemons.
- SystemVersion.plist: Stores OS version information.
- /etc/hosts: Maps hostnames to IP addresses, often modified for ad-blocking or development.
- .dmg and .plist files: Disk image and property list files used for app installation and configuration.
System files in macOS are protected by System Integrity Protection (SIP), which can be disabled via Recovery Mode for advanced users.
Core System Files in Linux Distributions
Linux distributions vary, but they share common critical files:
- vmlinuz: The compressed Linux kernel image.
- initrd.img: Initial RAM disk used during boot to load necessary modules.
- /sbin/init or /lib/systemd/systemd: The first user-space process.
- /etc/fstab: Defines how disk partitions are mounted.
- /etc/passwd and /etc/shadow: Store user account information and encrypted passwords.
- /var/log/: Directory containing system logs like
syslogandauth.log.
On systemd-based systems, unit files in /etc/systemd/system/ control service behavior.
How to View and Access System Files Safely
While system files are usually hidden, there are legitimate reasons to view or modify them—such as troubleshooting, customization, or learning. However, doing so requires caution.
Enabling Hidden Files and System File Visibility
By default, system files are hidden to prevent accidental changes. To view them:
- Windows: Open File Explorer > View > Options > Change folder and search options > View tab > Uncheck “Hide protected operating system files” and check “Show hidden files”.
- macOS: Use Terminal:
defaults write com.apple.finder AppleShowAllFiles YES, then restart Finder. - Linux: In most file managers, press
Ctrl+Hto toggle hidden files. Terminal:ls -ashows all files, including dotfiles.
Note: Modifying system files without understanding their function can lead to system crashes. Always back up first.
Using Command Line Tools to Inspect System Files
The command line offers powerful tools for examining system files:
- Windows (Command Prompt/PowerShell):
dir /alists all files, including hidden and system ones.sigverifchecks the integrity of system files.sfc /scannowscans and repairs corrupted system files.
- Linux (Terminal):
lsattr /path/to/fileshows file attributes, including immutable flags.file /bin/bashidentifies the file type.stat /etc/passwddisplays detailed file metadata.
- macOS (Terminal):
ls -lO /Systemshows file flags likerestrictedorimmutable.plutil -p /Library/Preferences/SystemConfiguration/preferences.plistparses plist files.
These tools help diagnose issues without altering files.
Safe Methods to Modify System Files
If you must edit a system file, follow best practices:
- Always create a backup:
cp /etc/fstab /etc/fstab.bak(Linux/macOS) or copy-paste in Windows. - Use elevated privileges only when necessary:
sudo nano /etc/hosts. - Verify syntax before saving—e.g., test
fstabwithmount -a. - Use trusted editors: Notepad++ (Windows), nano/vim (Linux/macOS).
For Windows, consider using the built-in System File Checker (SFC) tool to restore files to their original state if something goes wrong.
Risks of Tampering with System Files
While curiosity is natural, modifying system files without proper knowledge can have severe consequences. The risks range from minor glitches to complete system failure.
Common Consequences of Unauthorized Changes
Altering system files can lead to:
- Boot Failure: Corrupting
bootmgrorBCDcan prevent the OS from starting. - Blue Screen of Death (BSOD): Caused by faulty drivers or kernel modifications.
- Application Crashes: Removing or corrupting DLLs can break multiple programs.
- Security Vulnerabilities: Disabling SIP or modifying
/etc/passwdcan expose the system to attacks. - Data Loss: Incorrect
fstabentries might mount the wrong partition, overwriting data.
In enterprise environments, unauthorized changes can violate compliance policies and lead to audits.
Malware Targeting System Files
Malware often targets system files to gain persistence or disable security:
- Rootkits: Replace or hook into system files like
ntoskrnl.exeto hide malicious processes. - Ransomware: Encrypts critical system files to prevent recovery.
- Bootkits: Infect the Master Boot Record (MBR) or EFI partition, surviving OS reinstalls.
- Trojans: Modify
hostsfile to redirect traffic to phishing sites.
For example, the Kediakrypt ransomware specifically targets system files to increase damage.
How to Recover from System File Corruption
If system files are damaged, recovery options include:
- Windows: Run
sfc /scannowto repair corrupted files. UseDISM /Online /Cleanup-Image /RestoreHealthfor deeper repairs. - macOS: Boot into Recovery Mode and use Disk Utility to repair permissions. Reinstall macOS if needed.
- Linux: Use
fsckto check filesystem integrity. Reinstall packages viaapt install --reinstallorpacman -S.
Regular backups using tools like Windows Backup, Time Machine, or rsync are essential for quick recovery.
System Files and Security: A Critical Connection
System files are a prime target for attackers because compromising them grants deep control over the system. Protecting them is a cornerstone of cybersecurity.
How System Files Are Protected from Unauthorized Access
Operating systems use multiple layers of defense:
- File Permissions: In Linux,
/etc/shadowis readable only by root. - Digital Signatures: Windows verifies signatures on drivers and system binaries via Code Integrity.
- Access Control Lists (ACLs): Define granular permissions on files and folders.
- Secure Boot: Ensures only signed bootloaders and kernels are loaded, preventing bootkits.
For instance, Microsoft’s Kernel-Mode Code Signing Policy mandates signed drivers on 64-bit systems.
Role of Antivirus and Endpoint Protection
Modern antivirus software monitors system files in real-time:
- Behavioral analysis detects suspicious modifications.
- Heuristic scanning identifies unknown threats.
- Rollback features restore files to a clean state.
Solutions like Windows Defender, Malwarebytes, and CrowdStrike use cloud-based intelligence to respond to emerging threats targeting system files.
Best Practices for Securing System Files
To keep your system files safe:
- Keep your OS and software updated.
- Use strong passwords and enable multi-factor authentication.
- Avoid running as an administrator unless necessary.
- Enable Secure Boot and TPM for hardware-level protection.
- Regularly audit system file integrity using tools like
tripwire(Linux) orWindows Defender Application Control.
These practices significantly reduce the risk of compromise.
Advanced Tools for Managing System Files
For power users and IT professionals, specialized tools provide deeper insight and control over system files.
System File Checker (SFC) and DISM in Windows
These are essential for diagnosing and repairing Windows system files:
- SFC (System File Checker): Scans all protected system files and replaces incorrect versions with correct ones from the cache.
- DISM (Deployment Image Servicing and Management): Repairs the Windows image itself, which SFC relies on.
To run: Open Command Prompt as admin and type sfc /scannow. If SFC fails, run DISM /Online /Cleanup-Image /RestoreHealth first.
chkdsk and fsutil for Disk and File Management
These tools help maintain the health of the filesystem where system files reside:
- chkdsk: Checks disk integrity and fixes logical errors. Run
chkdsk C: /f /rto repair bad sectors. - fsutil: A powerful utility for managing NTFS features like reparse points, hard links, and file allocation.
For example, fsutil repair query C: checks if volume repair is enabled.
Third-Party Tools for System File Analysis
Several advanced tools help analyze and manage system files:
- Process Explorer (Microsoft Sysinternals): Shows which processes are using specific system files.
- AutoRuns: Displays all programs, services, and drivers that start automatically, including those modifying system files.
- Everything by VoidTools: Instantly searches all files, including system ones.
- Wireshark: While not a file tool, it can monitor network activity triggered by system processes.
These tools are invaluable for troubleshooting and forensic analysis.
Troubleshooting System File Errors
Even with protections, system files can become corrupted due to hardware failure, power outages, or software bugs. Knowing how to diagnose and fix these issues is crucial.
Common System File Error Messages
You might encounter errors like:
- “Windows cannot start because the following file is missing or corrupt: WINDOWSSYSTEM32CONFIGSYSTEM”
- “Invalid Boot Configuration Data”
- “NTLDR is missing” (older Windows)
- “Kernel panic: VFS: Unable to mount root fs” (Linux)
- “macOS could not be installed on your computer”
These often indicate corruption in critical system files or misconfigured boot settings.
Step-by-Step Fixes for Corrupted System Files
Follow these steps to resolve common issues:
- Boot into Safe Mode or Recovery Environment.
- Run
sfc /scannow(Windows). - If SFC fails, run DISM to repair the image.
- Use
bootrec /fixmbr,bootrec /fixboot, andbootrec /rebuildbcdfor boot issues. - On Linux, boot from a live USB and run
fsck /dev/sda1. - Reinstall GRUB if the bootloader is damaged.
Always back up data before attempting repairs.
When to Reinstall the Operating System
If system file corruption is widespread and cannot be repaired, a clean OS reinstall may be the only solution. This ensures a fresh, stable system. However, it should be a last resort after exhausting all other options.
What are system files?
System files are essential components of an operating system that enable it to boot, run applications, manage hardware, and maintain security. They include executables, drivers, libraries, and configuration files.
Can I delete system files to free up space?
No, deleting system files can cause your OS to become unstable or unbootable. Use built-in tools like Disk Cleanup or Storage Sense to safely remove temporary files instead.
How do I fix corrupted system files in Windows?
Run the System File Checker by opening Command Prompt as administrator and typing sfc /scannow. If that fails, use DISM: DISM /Online /Cleanup-Image /RestoreHealth.
Are system files the same across all operating systems?
No, each OS has its own set of system files. Windows uses .dll and .sys files, macOS relies on Unix-based components and plist files, and Linux uses .ko modules and shell scripts.
Why are system files hidden by default?
They are hidden to prevent accidental deletion or modification, which could destabilize the system. Only advanced users should access them, and even then, with caution.
System files are the invisible foundation of your computer’s operation. From booting up to running apps and securing your data, they play a vital role. While they’re protected by design, understanding their function, location, and risks empowers you to maintain a healthy, secure system. Whether you’re troubleshooting, optimizing, or just curious, respecting system files is key to a smooth computing experience.
Recommended for you 👇
Further Reading: